Packet capturing and analyzing network traffic is essential for organizations. As a Cybersecurity analyst, you have to examine, investigate, and block threats and unauthorized attacks using various SIEM tools and network analyzers – one of them is Wireshark.
Analyzing DNS requests of your network using Wireshark involves capturing DNS traffic and then examining the relevant packets. Capturing and analyzing appropriate packets gives you a detailed insight into the domain names being queried.
Below are the step-by-step instructions with screenshots that I’ve taken on my Windows Laptop:
AO in the below guide I’ll be capturing packet traffic between my Phone and Smart TV set. I have a smart Android TV with multiple Android-installed apps. I’ll use the Google Home app to control TV settings from my phone and will capture the traffic between the Phone and the TV.
I can make use of Multiple IP filters to filter the IP between a source and the destination. You can follow my other comprehensive guide for, incident response – where I’ve thoroughly explained how to isolate traffic between two devices using Wireshark IP and port filters.
Capture DNS Traffic:
- Open and Start the Wireshark tool on your PC and select the network interface through which DNS traffic is expected to flow. Like, I’ve selected my WiFi network in the below screenshot.
- Double-click on the interface name (mine is WiFi) to begin capturing packets.
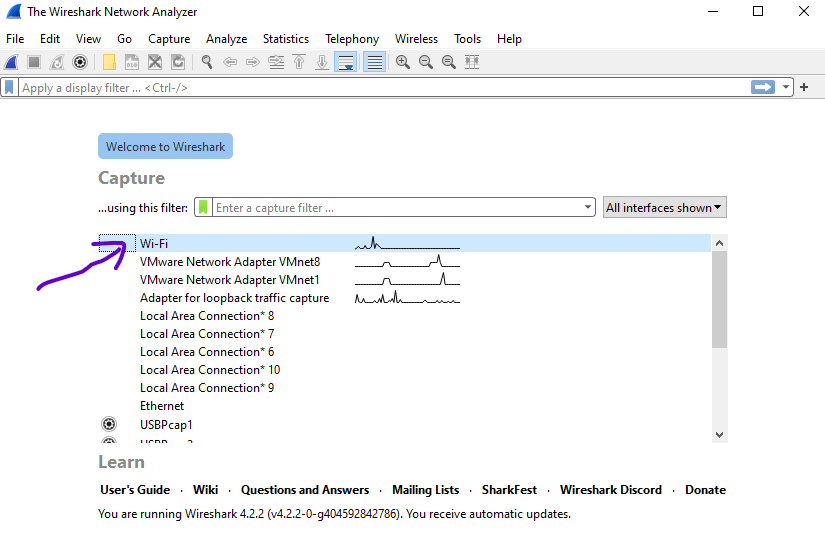
Now you have to, Filter DNS Traffic:
- To focus on DNS traffic, use the display filter: dns
- Just write dns in the search bar and press enter.
- Apply this filter in the display filter toolbar to view only DNS-related packets.
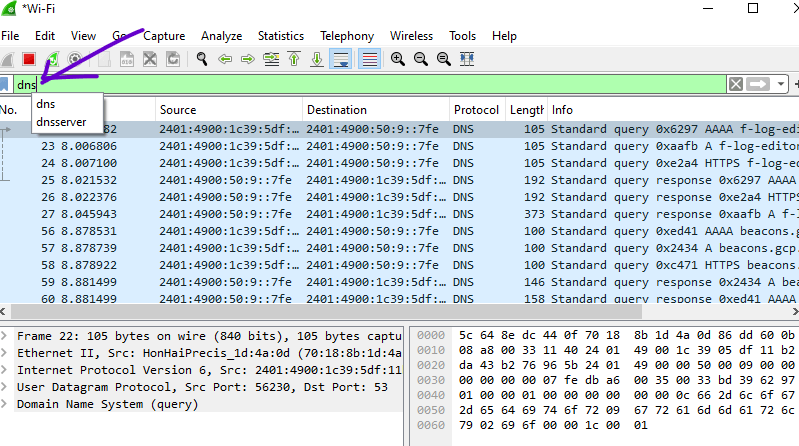
Now you have to, Examine DNS Requests:
- Look for DNS packets in the packet list pane.
- The “Info” column provides a summary of each packet. DNS queries will typically have the domain name in this column.
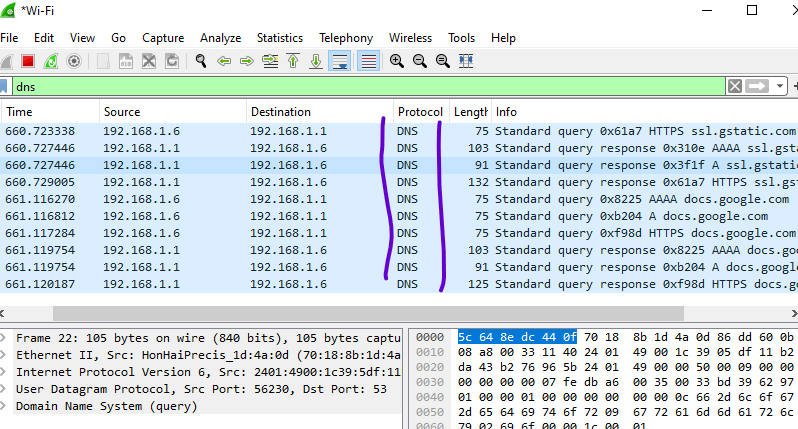
View DNS Query Details:
- Select a DNS packet in the packet list according to your preference.
- Double click on the packet and look for the, “Domain Name System (query)” section. You will have to scroll down and you’ll find it under IPV4 /User Datagram protocol.
- This area provides details about the DNS query, including the queried domain name.
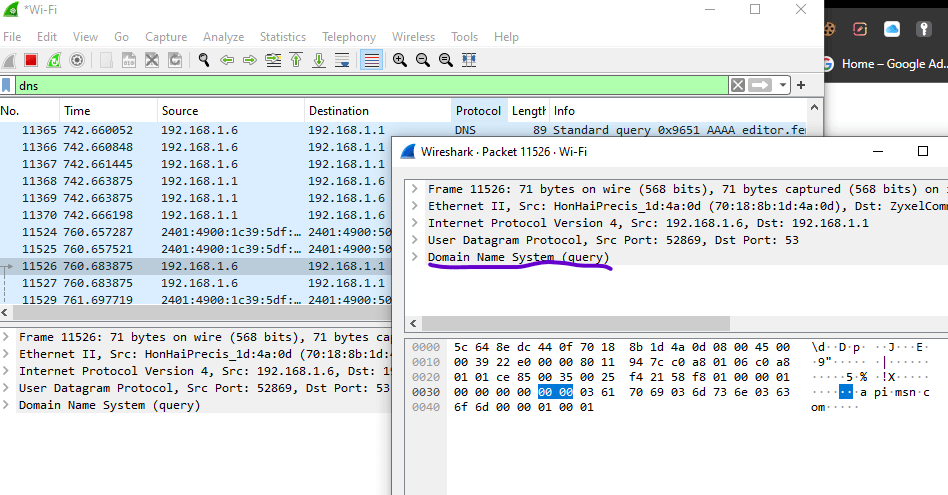
So in the below screenshot, I’ve clicked on the IP “192.168.1.6” which is my TV address. Now under the DNS query section, you can see that it is showing api.msn.com.
Since I’m using MSN app on my Android TV it is returning the name server of that specific connection.
Use a Display Filter for a Specific Domain:
- To filter for a specific domain, you can use a display filter like: dns.qry.name == “example.com”
- Replace “example.com” with the domain you are interested in.
Analyze DNS Responses:
- You can then analyze and observe various DNS responses to see if they match the queries.
- DNS responses typically contain information about the resolved IP address.
Follow DNS Streams:
- Right-click on a DNS packet and select “Follow” > “DNS Stream.”
- This will display the entire DNS conversation, making it easier to track the flow of queries and responses.
Inspect TTL (Time to Live):
- Check the “Time to Live” field in DNS responses. A low TTL might indicate a short-lived record, possibly associated with dynamic or suspicious behavior.
You can also, Identify Unusual Patterns:
- Look for patterns such as frequent DNS queries to the same domain, especially if the queried domain seems suspicious or unfamiliar.
Check for Unencrypted Queries:
- If DNS queries are sent in plain text (not encrypted), sensitive information may be exposed. Filter for unencrypted DNS traffic by using a display filter like: dns.flags.response == 0 && dns.flags.rcode == 0
Analyze Timing:
- Consider the timing between DNS queries. Rapid, repetitive queries or queries at unusual intervals might indicate malicious activity.
Apply Filters for Specific IP Addresses:
- If you are interested in DNS traffic for a particular device, use display filters such as ip.src == 192.168.1.2 to focus on DNS traffic from a specific IP address.
Use Statistics:
- Wireshark provides statistical information. Navigate to “Statistics” > “Resolver” to view DNS statistics, including the most queried domains.


