In the cybersecurity domain finding and investigating vulnerabilities within a network or your connected devices is an essential step toward fortifying your digital defense, be it for an employer, for your organization, or just for your personal privacy.
As I recently joined a cybersecurity internship program at a premiere cybersecurity institute, I investigate software and web services to make sure that the web is a safer place.
A recent comprehensive test by me with the help of Wireshark and other packet transfer protocols has revealed a significant vulnerability in iOS devices (with older versions of iOS) related to Wi-Fi MAC addresses, uncovering a plethora of privacy concerns.
Discovery of Vulnerability
I’ll delve straight into the details of vulnerability findings and their relation to the privacy threat. With the iOS 14 launch, Apple introduced the “Private Wi-Fi addresses” feature, to bolster user privacy. This same feature which is put forth to protect the MAC address of the iOS devices inadvertently exposed the real Wi-Fi MAC addresses of devices.
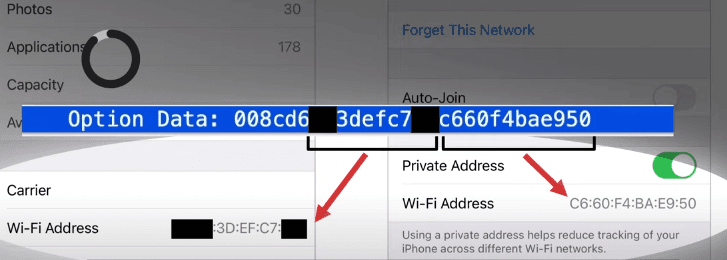
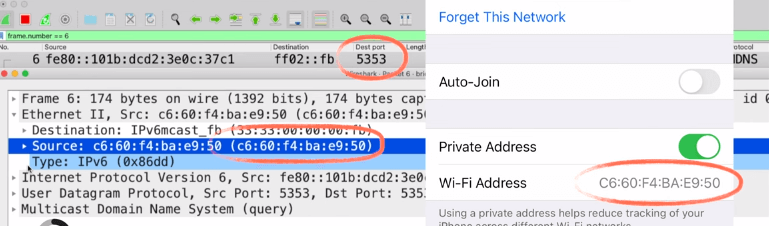
I identified this vulnerability using Wireshark’s packet sniffing and analyzed that when an iPhone connects to a network and initiates multicast requests to discover AirPlay devices within that network.
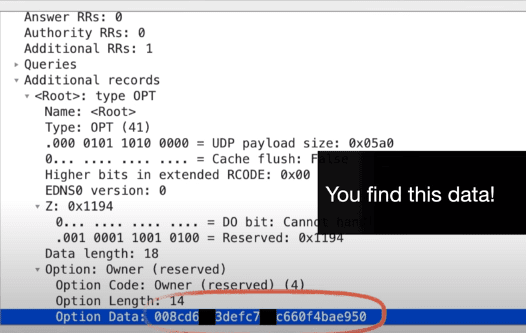
I was a bit surprised to see that, within these requests, iOS transmits the device’s authentic Wi-Fi MAC address, rendering it susceptible to tracking across various Wi-Fi networks. I also want to make clear that the iOS transmits the amalgamation of both the iPhone’s private and authentic MAC address.
Tools Which I Utilized in the Investigation:
- Wireshark: In my opinion, it is an excellent invaluable easy-to-use packet sniffing tool for capturing and analyzing network packets, providing detailed insights into the transmission of real Wi-Fi MAC addresses by iOS devices.
- tcpdump: Another similar tool to Wireshark, with tcpdump I intercepted and examined network traffic to easily identify and double-check the packets revealing genuine Wi-Fi MAC addresses during network activities thus dumping any doubts regarding the inconsistencies and any anomalies.
- Nagios and Zabbix: These two network monitoring tools played crucial roles in detecting anomalies/irregularities within network traffic (only works on the same Wi-Fi network), enabling the identification and recording of potential vulnerabilities associated with Wi-Fi MAC address exposure.
Impact and Resolution
The exposure of real Wi-Fi MAC addresses in iOS devices (even though the private Wi-Fi setting was enabled) posed a significant threat, enabling device tracking across Wi-Fi networks and monitoring device movements across various Wi-Fi networks.
Apple addressed this vulnerability in iOS 17.1 (CVE-2023-42846), effectively mitigating the issue and safeguarding user privacy.
Hackers and threat actors can also use this vulnerability to create new detailed user profiles, accumulate essential data, and target unauthorized surveillance and exploitation of location-based services.
Ethical Considerations
This discovery emphasizes the critical role of ethical cybersecurity exploration. Responsible disclosure of vulnerabilities to relevant parties, such as Apple’s security team, is essential to facilitate timely fixes and protect users.
The Introduction and Flaw
The feature which apple introduced in iOS 14 to enhance user privacy by generating unique MAC addresses per network in iOS devices, failed to conceal the device’s actual MAC address during AirPlay discovery requests, thereby rendering it ineffective in safeguarding user anonymity across networks.
iOS substitutes the genuine MAC address at the data link layer with a dynamically generated address specific to each network. Despite this, the vulnerability lies in the fact that the real MAC address remains embedded within the AirPlay discovery requests initiated by iPhones upon network connection.


